Are you having trouble finding 'decrypting cryptography essay'? You can find questions and answers on the topic here.
Table of contents
- Decrypting cryptography essay in 2021
- Encryption and decryption
- What is cryptography
- Basic cryptography techniques
- Cryptography pdf
- Symmetric encryption
- Asymmetric encryption
- Cryptography ppt
Decrypting cryptography essay in 2021
 This picture illustrates decrypting cryptography essay.
This picture illustrates decrypting cryptography essay.
Encryption and decryption
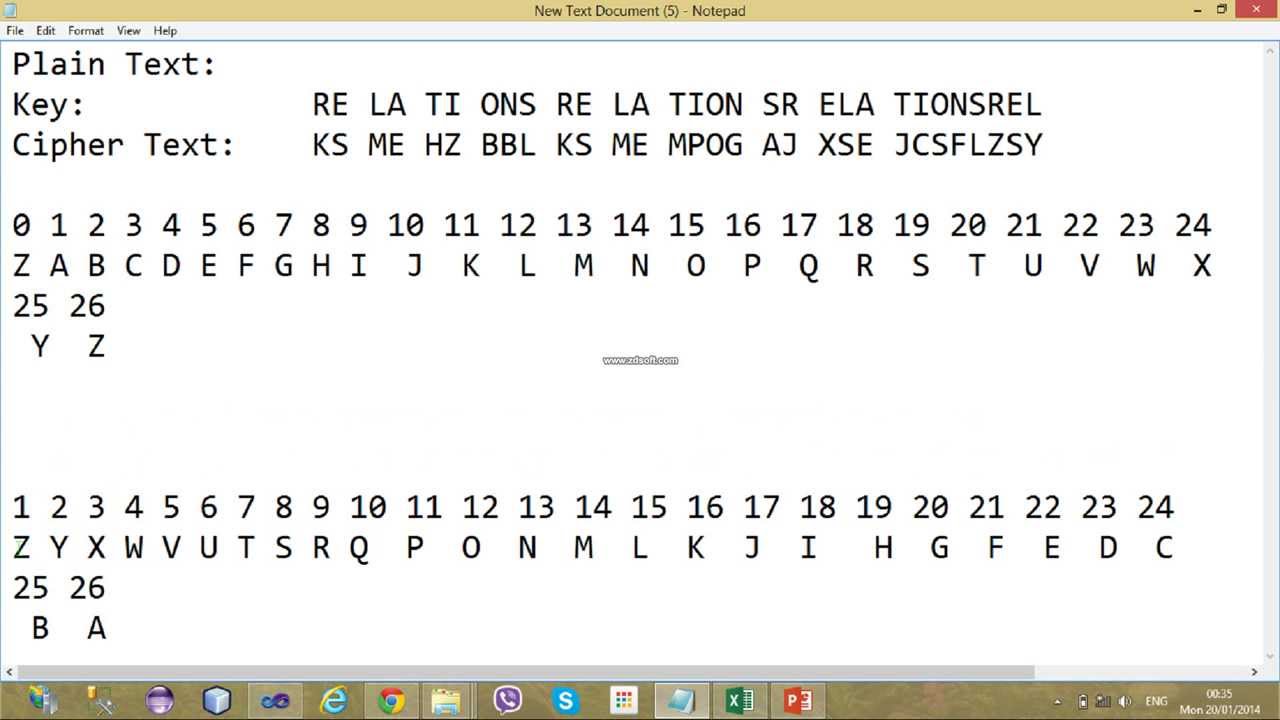 This picture shows Encryption and decryption.
This picture shows Encryption and decryption.
What is cryptography
 This image shows What is cryptography.
This image shows What is cryptography.
Basic cryptography techniques
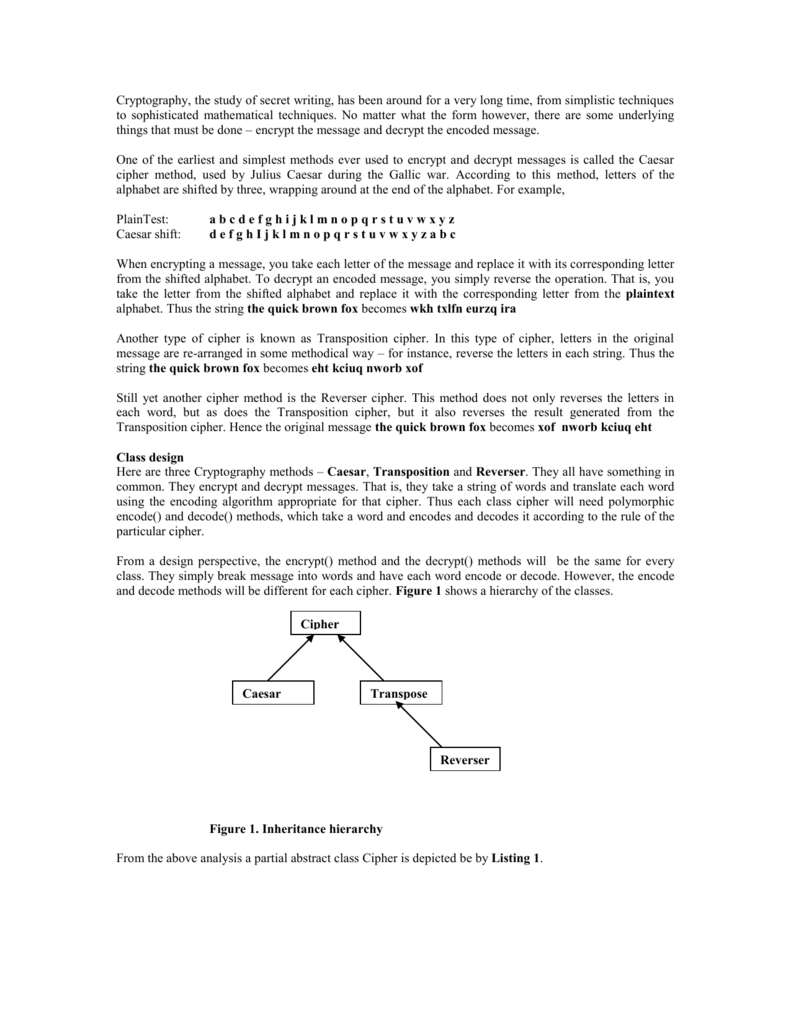 This image shows Basic cryptography techniques.
This image shows Basic cryptography techniques.
Cryptography pdf
 This image shows Cryptography pdf.
This image shows Cryptography pdf.
Symmetric encryption
 This image demonstrates Symmetric encryption.
This image demonstrates Symmetric encryption.
Asymmetric encryption
 This image shows Asymmetric encryption.
This image shows Asymmetric encryption.
Cryptography ppt
 This image illustrates Cryptography ppt.
This image illustrates Cryptography ppt.
What is the purpose of public key cryptography?
Public-key cryptography is a fundamental and widely used technology around the world, and enables secure transmission of information on the internet and other communication systems; this concept was proposed in [15]. It is also known as asymmetric cryptography because the key used to encrypt a message differs from the used to decrypt it.
Is the art of cryptography born with writing?
The art of cryptography is considered to be born along with the art of writing. As civilizations period started, human beings got incorporated in tribes, groups, and kingdoms. This led to outgrowth of ideas such as power, battles, supremacy, and politics.
What's the difference between Decryption and cipher text?
Decryption: The technique of altering cipher text or encrypted text into plain (original) text is called as Decryption with the help of same key or other key.Key: An amount of information used for encrypting and decrypting text.Cipher text: The message written in secret code and is not understandable by anyone.
Which is an introduction to encryption and decryption?
1.1 An introduction to Encryption and Decryption, a type of cryptography Encryption and Decryption, a type of cryptography, refers to the process of scrambling information so that the observer cannot be detecting the data. Cryptographic key is a piece of data used to encrypt or decrypt to plaintext.
Last Update: Oct 2021